At the end of April Charles presented this talk to the wonderful folk at the Forbes House Museum in the US. Over the course of an hour, Charles tells the tale of Dunans and outlines the next steps in the restoration.


At the end of April Charles presented this talk to the wonderful folk at the Forbes House Museum in the US. Over the course of an hour, Charles tells the tale of Dunans and outlines the next steps in the restoration.
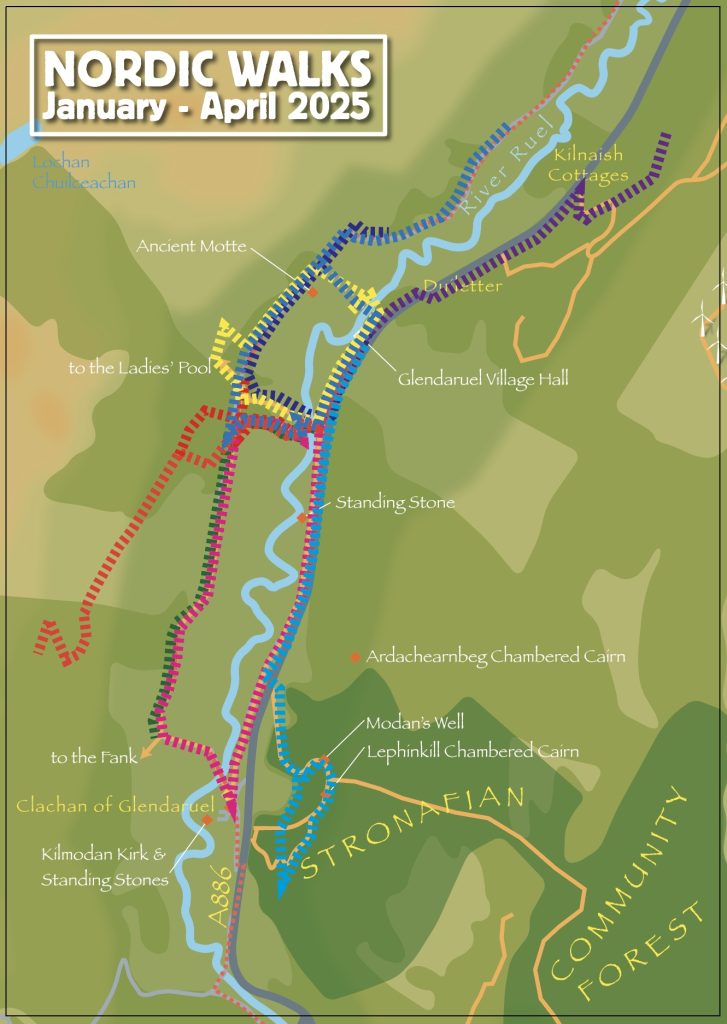
A local group has been walking from the Glendruel Hall this year, and here is the screen capture from a map I have been drafting – derived from the main community map used in signage and on newsletters, plus the various strava, garmin and OS records the walkers have taken each week.
Have to say I was a *little* premature on declaring success. I’ve got a couple of updates to my previous post about this pernicious WordPress hack (Disinfecting for WPYII2 – the #fakeplugin invading WP and how to kill it #wpyii2 #killwpyii2).
I am happy to report all websites are now clear and functioning perfectly, even the ones on deprecated versions of WP, plugins and themes.
I’ve just spent a week disinfecting my server from this pernicious bit of ruskyhack. Not only has it completely derailed my working week, its meant that my team have had very little work over that period as my websites have been unable to process orders. Whoever the surnames Skorobogatov, Serebryakov and Biryukov refer to, well, they should be ashamed of themselves.
The context is this. On a server (not the one this blog is hosted on) I have c. twenty installs of WordPress, plus several apps which are collected in three or four directories. I’ve got a variety of domains and subdomains, as well as password-protected directories for particularly sensitive work apps.
Now if I say that some of these apps take data from my WP install DB repackage it and spit it out via the Royal Mail API into their Click and Drop app, you will get why this fake plugin has completely disrupted that workflow. And of course the problem with some of the WP installs I am using is that, because of its wide integration into our production systems, I cannot upgrade either the WordPress version or the plugins associated with it.
WPYII2 found its way onto the server mid-week last week and the first I knew about it was some code appearing at the top of the homepage of several of my sites.
The damage was extensive. I lost three separate bespoke apps we use regularly for business because the fake plugin deletes top level ‘index.php’ files when they are not associated with a WP install. Luckily I had different earlier iterations available on the server so I could cobble together replacements – which ended up improving on the earlier versions.
As for the WP installs, well, they all fell over, repeatedly. I ended up playing whack-a-mole for a couple of days while trying to understand what the hell was going on. It didn’t help that there were plenty of posts from security firms saying, yes, this is a thing, and we’re here to help you get rid of it, but very few saying this is how you do it. I *think* I have done it, and the solution has ended up being cobbled together through trial and error and some helpful non-specific security posts from a variety of sources [for example]
So how to rid your WP install of this vicious fakery?
As of 15th June 2022 I seem to have reached a stable environment with the fake plugin effectively being locked out by the abovenoted steps. However, I continue to monitor the server, and use downnotifier.com to give me immediate intel if things go awry. Any recommendations on other steps to keep this stuff away, let me know!
The cost of all of this to my business? Who knows? My time / stress? The lost orders? The lost IP? Those who black hat hack should reflect on their lives and wonder whether their skills could be better used elsewhere.

Over the last month, watching the horror of Putin’s unwarranted invasion of Ukraine, the horror has emerged on the page. The mad bear was obvious. Dancing While No-One is Watching and Lost In The Woods not so much until the gimlet eyes starting appearing.




As web developer and visual designer I’ve been working on ZippedyZoom.club which is part of TWTC’s response to Covid-19 – providing both a portal for kids to access fun activities and awesome stories, and a place for creative practitioners of all sorts to keep working. With funding for an initial 12-week run, we’re focussed on delivering content beyond that endpoint. Have a look here.
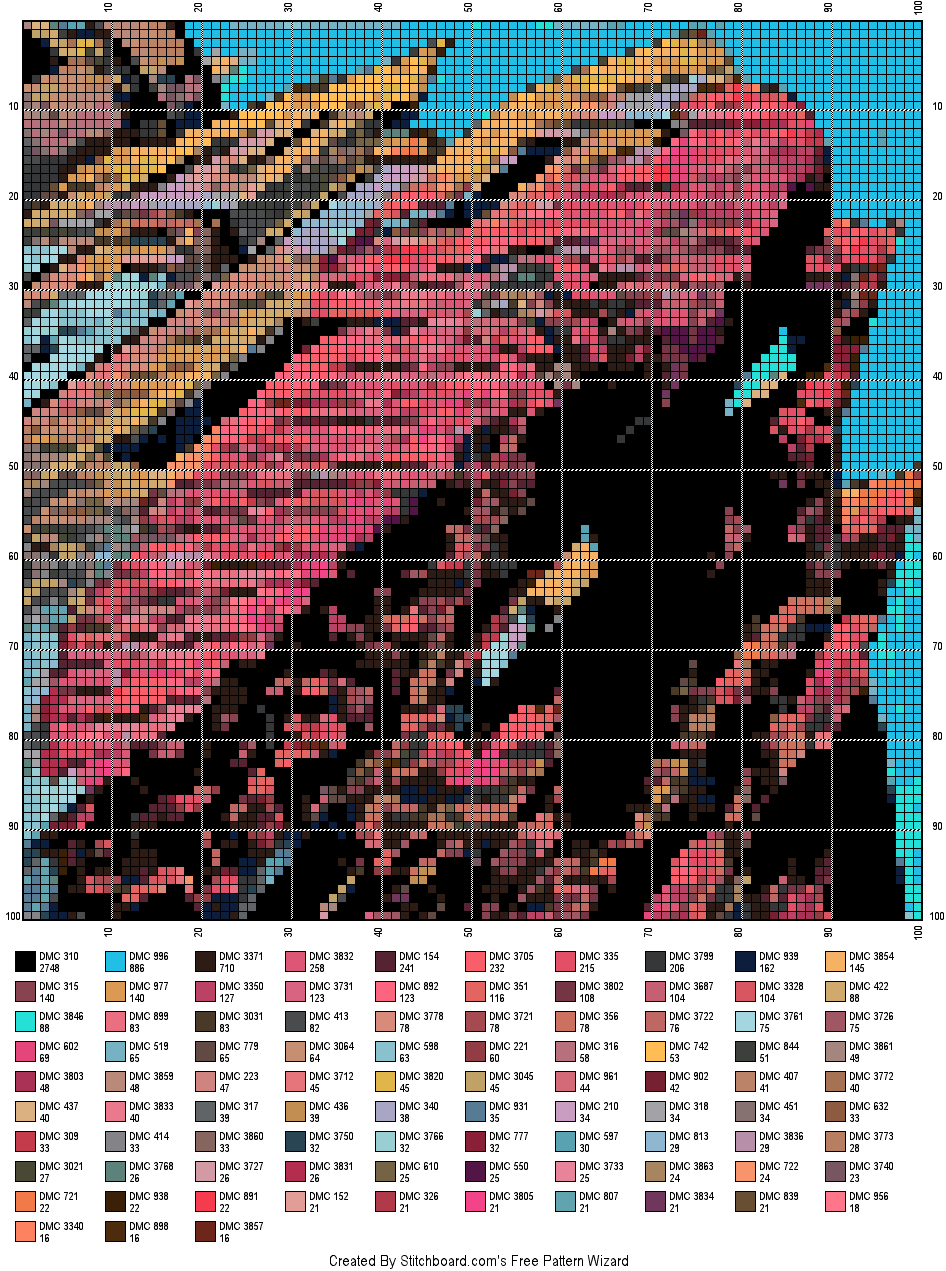
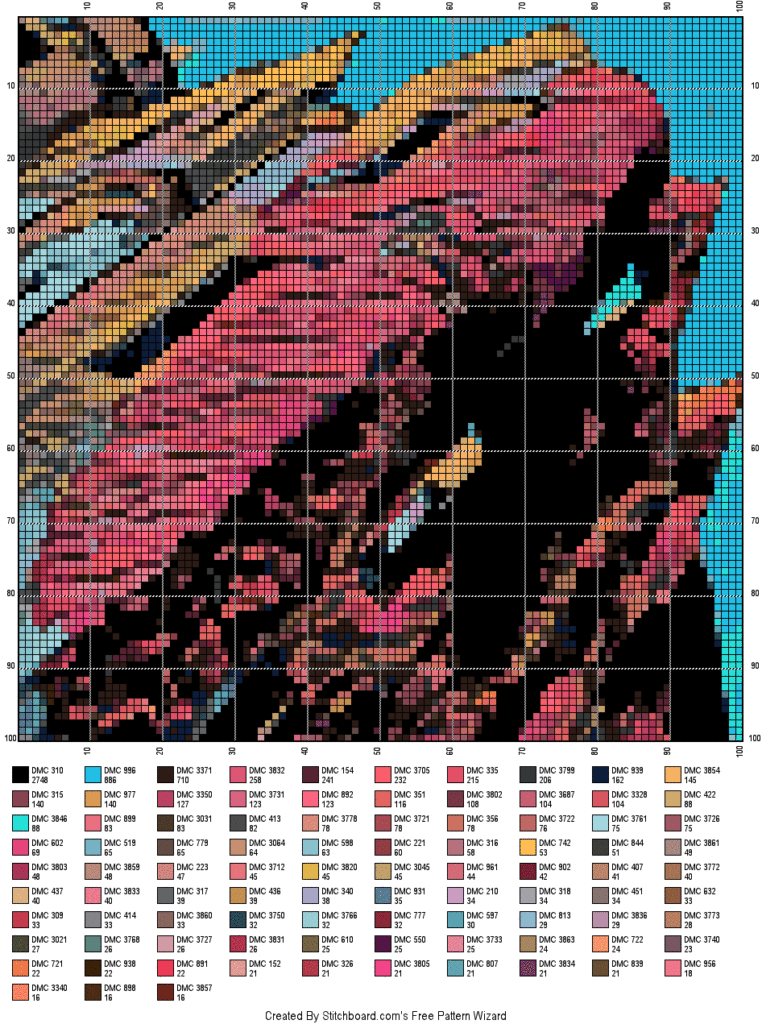
After several requests, and given that we are nearing the festive season, I thought I would finally try my hand at developing a cross-stitch pattern! The results can be found here and below is a gif of the unrestricted palette version (you’ll need 95 colours!!).

Readers will be aware of my ongoing design and illustration work, as well as installations and videos I have produced over the years. Last year, inspired by a series of illustrations I produced prior to delivering a show in Birmingham, I launched Selwyn & Ink a portfolio website and overall brand to encapsulate this work and separate it from ScottishLaird and Dunans Castle. The website is available here.
One of TWTC‘s perennial favourites travels to Pitlochry this summer. A night not to be missed. I designed the poster, and also produced the video below – which will give you the idea!

We wanted to do something different with our signage, refresh it yes, but more than that. Reflect our ambition, create something familiar yet original. I think we’ve done it. (Please ignore the calibration and cropmarks!)